What is cyber forensics?
Cyber forensics, often referred to as computer forensics, is the process of extracting, analyzing, and preserving data that can be used as evidence in legal proceedings. Its aim is to uncover digital footprints of illegal activities, ranging from unauthorized data access to malicious hacking. First recognized in the 1980s, cyber forensics emerged alongside the rise of personal computing and quickly became essential for tackling digital crime.
Key Milestones in Cyber Forensics:
- 1986: The Computer Fraud and Abuse Act (CFAA) is passed.
- 1989: The International Association of Computer Investigative Specialists (IACIS) is established.
- 1992: The Computer Analysis and Response Team (CART) is created.
- 1995: The International Organization on Computer Evidence (IOCE) forms.
- 2000: The Regional Computer Forensic Laboratory (RCFL) is set up.
Importance of Cyber Forensics
CF plays a crucial role in:
- Legal Compliance: Ensuring that digital evidence is maintained with integrity.
- Incident Investigation: Helping correlate user activities with security breaches.
- Business Audits: Protecting company assets by investigating security breaches and policy violations.
Cyber forensics often works in tandem with cybersecurity but can involve more detailed investigation and evidence extraction for legal purposes.
How Does Cyber Forensics Work?
Cyber forensics goes beyond typical data collection. Investigators may require access from external auditors, executives, or court subpoenas to retrieve data. The key steps include:
- Identification: Determining what evidence is needed.
- Preservation: Maintaining the integrity and security of the evidence.
- Analysis: Uncovering insights from the data.
- Documentation: Creating a trail of all actions taken during the investigation.
- Presentation: Summarizing findings in a structured manner.
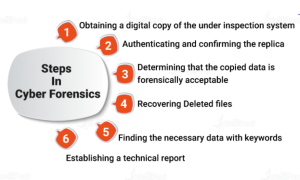
Process:
- Identification: What evidence is relevant to the case?
- Preservation: How to ensure data remains untampered?
- Analysis: What does the data reveal?
- Documentation: Document every step and piece of evidence.
- Presentation: Share findings in a legally acceptable format.
Challenges:
CF experts face a range of challenges, such as:
- Data Recovery: Encrypted or deleted data can be difficult to retrieve without encryption keys or proper tools.
- Cloud Visibility: Limited access to physical systems and data stored in cloud services.
- Network Log Overload: Big data from network logs requires advanced analytics to process.
- Jurisdiction Issues: Legal access to data stored in different regions.
Techniques in Cyber Forensics:
- Reverse Steganography: Uncover hidden information in files.
- Stochastic Forensics: Reconstruct digital activities without artifacts.
- Cross-drive Analysis: Compare multiple storage devices to piece together a narrative.
- Live Analysis: Access real-time data from volatile memory.
- Deleted File Recovery: Use specialized tools to recover lost data.
Types of CF:
- Network Forensics: Investigating network traffic.
- Email Forensics: Recovering deleted or hidden email conversations.
- Malware Forensics: Analyzing malware and hacking attempts.
- Mobile Forensics: Analyzing data from smartphones.
- Disk Forensics: Recovering data from storage drives.
The Future of Cyber Forensics
With more data privacy laws coming into effect, cyber forensics is becoming increasingly important. As cyberattacks rise, companies and individuals will need more support from CF experts to protect their data and take legal action.
For more insights on tech trends, check out our post on the Top 5 In-Demand Programming Languages for 2024. If you want to learn more about this and how it protects businesses, explore this guide.
